 TUV Rheinland, a leading expert in digital transformation and cybersecurity, today announced the results of a worldwide study, exploring how 370 industrial organizations protect their operational technology (OT) assets from cyberattacks. The findings show that as hackers increasingly attack OT, many companies are not aware of the threats cyberattacks pose to their OT assets. Moreover, their measures for cybersecurity are usually not tailored to operational technology.
TUV Rheinland, a leading expert in digital transformation and cybersecurity, today announced the results of a worldwide study, exploring how 370 industrial organizations protect their operational technology (OT) assets from cyberattacks. The findings show that as hackers increasingly attack OT, many companies are not aware of the threats cyberattacks pose to their OT assets. Moreover, their measures for cybersecurity are usually not tailored to operational technology.
Lack of concern toward OT cybersecurity is worrying
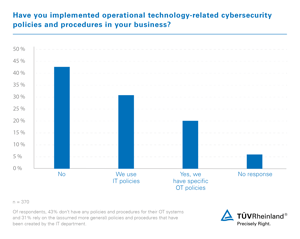
In the study entitled "Industrial Security in 2019: A TUV Rheinland Perspective", 40 percent of respondents stated that they had never assessed the risks posed by cyberattacks on their operational technology. A further 34 percent do not know whether their own company has ever investigated these risks. In addition, only one in five companies has tailored its measures for cybersecurity to operational technology. "The fact that OT cybersecurity is obviously not of high priority is worrying. Attacks from the Internet can shut down entire plants, which can result in production downtime and higher costs," comments Nigel Stanley, Chief Technology Officer, Operational Technology and Industrial Cybersecurity at TUV Rheinland.
Preventing hazards from the Internet
In the study, the authors emphasize the complexity of OT security in a networked world. For instance: Enterprise IT applications are constantly updated to respond to new threats. But computer controls for OT systems are not typically updated regularly. "Whether or not an OT system is connected to the Internet, preventive cybersecurity measures based on an understanding of the OT risk are a must. This is especially important as the safety of OT systems can be undermined by cybersecurity attacks," says Nigel Stanley.
Protecting production data from theft
Those responsible should think about how to protect their own production facilities from physical intrusion. "Whoever is responsible for OT security should consider whether an intruder could insert a rogue USB stick into a system," Stanley says. "A lot of valuable intellectual property is found in industrial plants and data theft can be just as rewarding for some hackers as disrupting the plant production line."
Operational Technology (OT)
Operational technology is name given to the computerized systems used to control physical assets such as valves, motors and pumps. Its use is prevalent across many industries and sectors including oil and gas, transportation, building management systems, water treatment plants and critical national infrastructure. Experts from TUV Rheinland already have identified Operational Technology as a frontline for cyberattacks in their Cybersecurity Trends.
The study
The study was conducted by IT analysts from Bloor Research, who administered an online survey to 370 managers from companies worldwide, inquiring about how they protect their OT assets. While almost 70 percent of the respondents work in the manufacturing industry, a variety of other industries were also represented, including automotive, oil and gas, telecommunications, energy, chemical, logistics and public institutions. The study looks at the aspects of risk assessment, protection against and detection of cyberattacks, and provides information on protective measures and the recovery of assets after a cyberattack. The free study can be downloaded here.
Digital Transformation & Cybersecurity
For over 20 years, TUV Rheinland's Digital Transformation & Cybersecurity Business Stream has been helping companies from various industries, government agencies and public institutions to use innovative technologies securely. With nearly 1,000 consultants worldwide, our experts have a high level of industry knowledge about digital transformation and cybersecurity. In an increasingly vulnerable world of networked systems and devices, our cybersecurity solutions aim to combine security and data protection. Our team carries out cybersecurity tests, industrial security tests and data protection tests on the Internet of Things (IoT) and cloud infrastructures, among others.


