Cyber Security may not be a new term for the general public, but it is definitely a new world altogether in the industrial sector. It has never been an issue for traditional factories or plants before, since the machines and production lines are disconnected from the internet. However, the concept of traditional manufacturing is gradually getting obsolete, and you need to change your perspective in the way you run your plants.
As we are evolving into Industry 4.0., we are entering an uncharted territory where suddenly all the Industrial Control Systems (ICS) are connected to each other and to other systems across the worldwide web as well. A lot of efforts have been placed into the technology aspect to bring industrial automation to a whole new level, but most operators have only put minimum attention in the topic of industrial cyber security.
Venturing into an unknown territory of industrial cyber security can be an overwhelming experience. To illustrate it simply: it is a big word in an obscure world. More often than not, operators do not even know where to start.
If this is what you are facing, fear not, these three pointers from Mr. Heinz Gall, TÜV Rheinland expert in Functional Safety and Cyber Security, will provide you a structured approach and you will be on the high ground in connecting Functional Safety with Cyber Security.

1) Qualified and reliable products
When we are talking about Industrial Control System (ICS), it has always been about the hardware, firmware and software. These system elements often require significant investment, but you know it will pay off if you have a reliable, qualified equipment (i.e. able to perform in stable and predicted manner given the common operational scenarios) to run your production plants.
After you have a reliable equipment in place, the next step is to assess and qualify their interoperability, to ensure that they can work together in a system. When it is no longer an issue to assess the functionality of the system, you should start to take Cyber Security aspect into account in your product development and plant assessment.
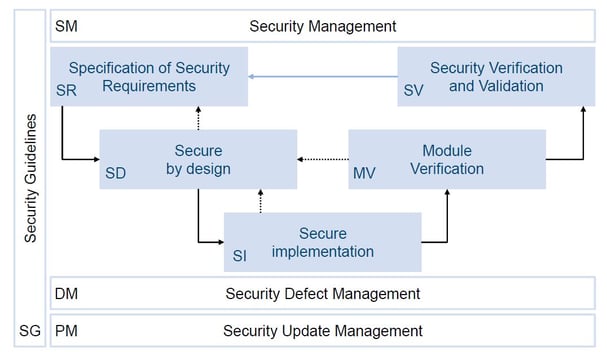
2) Safety and Security Management throughout all life cycle phases
Companies who implemented Safety or Security Management System for the sake of compliance are missing the big picture. Like any management systems, Security Management System cannot exist exclusively on its own. It must be managed from a bird’s-eye view perspective encompassing different aspects of the stages and stakeholders, and not simply operational. Security Management requires technical, as well as organizational measures.
3) Competent people involved in any activity
Plants and processes are run by people, so it is inarguable that they hold a crucial role in making a plant operation safe and secure. We all know that people carries an inherent risk of human errors, but all of us will agree that competent people make less common errors. Another widespread observations across different plants: many disruptions occurred because people overlooked or misjudged a certain protocol, because they did not have the full knowledge of the system and the implications in different operational scenarios, because they were not fully competent in their field of work.
Training is naturally the first proposed course of action to address such situation, but ‘trained’ does not always mean ‘competent’. You also need to make sure that the personnel is assessed, qualified, having adequate field experience, and regularly following up with the new technology and practice.

These insights were presented by Mr. Heinz Gall in the Asia ICS Cyber Security Conference 2017 in Singapore. You can view the presentation slides and other infotmation from the 'more information' section below.
More information
- Get a copy of Mr. Heinz Gall's ‘Structured approach to Functional Safety and Cyber Security’ Presentation.
- Read the summary of panel discussion in Asia ICS Cyber Security Conference 2017.
- Find out Cyber Security services that TÜV Rheinland offers, please visit our service page.
- Need help on Functional Safety and/or Cyber Security? Ask TÜV Rheinland.
- Keep up-to-date to changes in regulatory and standards by subscribing to our mailing list.


