Thousands of machines infected by the global NotPetya ransomware outbreak.
Patch your systems to avoid being the next victim.
WHAT'S HAPPENED?
The campaign seems to have originated in the Ukraine and is now spreading globally. The NotPetya
ransomware is a hybrid of Win32/Petya [1] and WannaCry.[2] The attack vector appears to be MS Office
documents and it attempts to spread itself to other computers using both MS17-010 (WannaCry[3]) and
system tools like PsExec and WMI[4] which allow commands to be executed remotely. NotPetya also
checks for cached administrator credentials and attempts to authenticate to other machines.
WHO IS IT AFFECTING?
The Ukraine government, banks, and electricity grid were initially hit hardest. Also, the Ukraine state
power utility and Kiev’s airport and metro system were affected. The ransomware is spreading rapidly
and companies in France, Denmark and the US have also been effected. The radiation monitoring
system at Chernobyl was reportedly taken offline.
WHAT IS IT AND WHY HAS IT BEEN SO EFFECTIVE?
Similar to WannaCry, NotPetya exploits a known vulnerability in Microsoft Windows Server Message
Block (SMB) protocol [CVE-2017-0145] which allows for remote code execution on a vulnerable system.
Code named 'EternalBlue,' this exploit was stolen from the NSA's Equation Group and then later made
public by the Shadow Brokers hacking group on April 14th, 2017. Microsoft issued a patch for this
vulnerability two months ago, on March 14th, 2017 [MS17-010].
What is notably different from WannaCry, is the inclusion of additional functionality designed to steal
cached credentials from the compromised local system and then use them to authenticate and run
commands on other remote systems on the local area network, resulting in potential propagation to
patched machines.
The Petya family of malware overwrites the victim computer's boot sector and makes it point to a separate operating system that performs the file encryption. [5] Infected computers display a message demanding a Bitcoin ransom worth $300. Those who pay are asked to send confirmation of payment to an email address. However, that email address has been shut down by the email provider.[6]
HOW DOES IT WORK?
The initiating attack vector is most likely a Phishing attack designed to trick users into running the
malware, or direct infection through the SMB exploit if a machine can be addressed. The threat arrives as a dropper Trojan that connects to 84.200.16.242 [7] and specifically /myguy.xls which is an HTA file. This drops another binary which contains the malware itself. There is also evidence of pass the hash
techniques, which potentially make it a serious threat inside a corporate network. There are multiple
droppers to include deploying via psexec, wmi and via Eternalblue for propagation.
Notably, the dropper checks for file "C:\Windows\perfc" and the threat does not infect the system further
with the ransomware. That kill switch method only works on the WMI/PSExec and is not full stop. This
characteristic of the dropper was identified by a security researcher in the Boston area. NotPetya then
creates a shutdown scheduled task, copies itself to %AppData\Temp%, and another file is dropped there
as well.
WHAT SHOULD YOU DO TO PROTECT YOUR ORGANIZATION?
To avoid becoming the next victim of the NotPetya ransomware outbreak, you should:
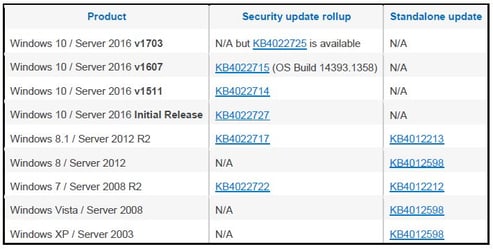
1. Start by patching your systems
For Windows 7 and Windows Server 2008 system, this means applying the MS17-010 patch to address
the SMBv1 Remote Code Execution vulnerabilities. Microsoft also released a patch for older operating
systems including Windows XP, Windows 8, and Windows Server 2003. Besides installing the updates,
Microsoft also advises that the SMBv1 protocol is disabled, as it is an old protocol that has been
superseded by newer versions. You should also consider adding a rule on your router or firewall to
block incoming SMB traffic on port 445.
MS17-010
2. Get your backups in order
One of the most fundamental protections against ransomware is the ability to restore from recent backups
reliably. You will want to have multiple backups, with the ability to rollback to any point in time, and these
should not be connected to the source machine, or they could get encrypted as well. Various cloud
service providers offer good options here, with many professional backup services available.
3. Reduce the likely success of phishing emails
Enable strong spam filtering to reduce the probability of phishing emails reaching end users. Authenticate inbound email using Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing. Educate your users and outline the dangers and the potential impact of ransomware on your business. Make them suspicious of every email they receive that they are not expecting, every link and every attachment.
4. Update monitoring capabilities
Update detection/prevention technologies with the latest signatures and implement appropriate indicators
of compromise within security analytics solutions, as they continue to become available.
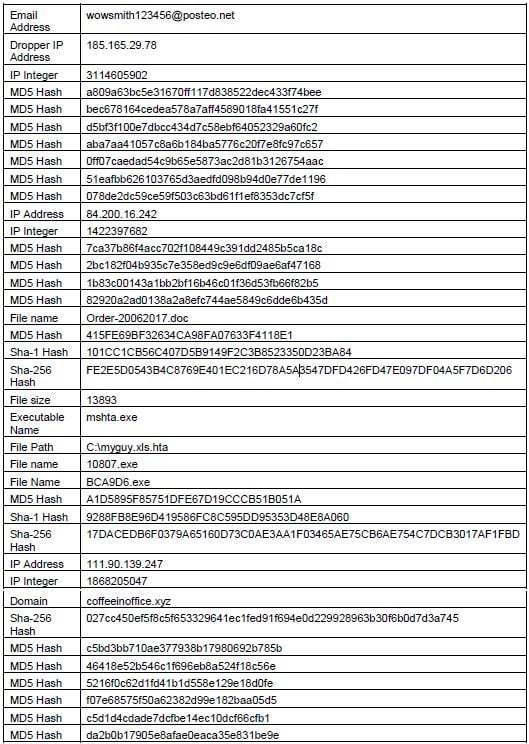
Indicators of compromise[8]
5. And if you become a victim?
If you do become a victim of the outbreak, do not pay the ransom. It only creates a viable market for
cyber criminals and motivates future ransomware attacks. In this case, it may not even be possible to
pay since the ransom email address was taken offline. Instead, implement internal incident response
processes to quickly contain propagation and contact law enforcement when appropriate. If
necessary, seek help from your trusted cybersecurity partner.
IF YOU NEED HELP?
Please contact one of our regional cybersecurity executives for immediate assistance.
North America
Tom Hazen
President, OpenSky Corp, TÜV Rheinland Company
Tel: +1 (413) 441-0147
E-mail: thazen@openskycorp.com
Europe (West, East, and Central)
Bjoern Haan
Managing Director, TÜV Rheinland i-sec GmbH
Tel: +49 174 1880240
E-mail: Bjoern.Haan@i-sec.tuv.com
Middle East, Africa, Asia Pacific
John Ramesh
Managing Director, TUV Rheinland L.L.C, Oman
Tel: +968 9423 4267
E-mail: john.ramesh@om.tuv.com
Sources:
1 https://www.microsoft.com/security/portal/threat/Encyclopedia/Entry.aspx?Name=Win32/Petya
2 https://nvd.nist.gov/vuln/detail/CVE-2017-0145
3 https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
4 End of Support.
5 https://labsblog.f-secure.com/2016/04/01/petya-disk-encrypting-ransomware/
7 https://gist.github.com/vulnersCom/65fe44d27d29d7a5de4c176baba45759
8 https://www.hybridanalysis.
com/sample/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745?environm
entId=100


