The cybersecurity field of operational technology (OT) is buzzing as companies increasingly realise that their production systems, manufacturing plants, chemical processing plants, or industrial control systems are at risk from cyber-attacks. This realisation is fuelled by a big uptick in hacker interest as such systems are insecurely connected to the internet and compromising them is a change from stealing credit card information.
In response to cybersecurity concerns, companies often claim that their OT systems are air gapped and not connected to the internet — so they are immune from cyber attacks via this route. The bad news is that upon further investigation, in almost all instances, such claims are found to be incorrect. The reality is that connections abound and systems light up with data flows without the company even knowing about it.
What Are Some of the Biggest Risks to OT Security?
The humble USB is renowned for bridging OT air gaps. Indeed the now infamous Stuxnet worm that was first revealed to the public in 2010 was believed to have been introduced into a “secure” facility by a USB stick. The rest is history. It is extremely common to find some form of USB port openly accessible on SCADA workstations or process engineering systems. These USB ports may be a route in for malware or a route out for corporate intellectual property. Either way, open USB ports are bad for the operating company.
The all-powerful smartphone is another convenient mechanism to cross air gaps when switched into Wi-Fi hotspot mode. There have been cases where bored operators will fire up a hotspot and stream dubious movies overnight when the control room is quiet. And we mustn’t forget the smartphone camera that can exfiltrate stacks of visual data useful to an adversary.
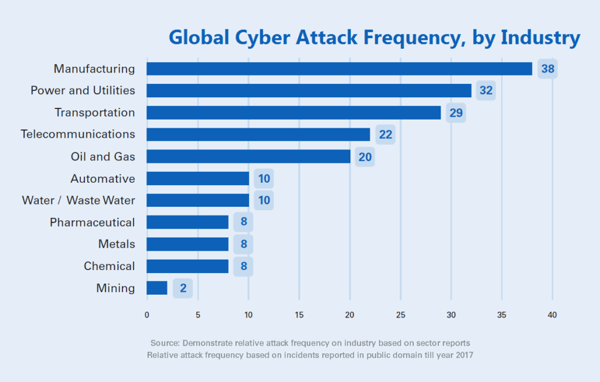
The image below shows cyber attack frequency by industry.
Has Your Wi-Fi Been Assessed for Risk?
Insecure Wi-Fi hotspots can leak large amounts of OT data before anyone realises it has happened. This vulnerability often comes down to bad configuration, or maybe a desire by the OT team to take advantage of an existing internet connection.
Certainly, insecure Wi-Fi hotspots are not always malicious as more and more OT equipment manufacturers need access to their hardware for predictive maintenance and similar reasonable business needs. But has the connection been assessed for risk?
Considering Other Means of Connecting to Your OT
A bit more pernicious than Wi-Fi is the increased use of cellular connections so that equipment can “phone home.” In many cases these connections are never spotted because of their small form factor and difficulty in spotting their transmissions. Many cellular connections are only found during a bug sweep — a site technical surveillance counter measures assessment.
Finally we have some esoteric ways of connecting OT kit to the internet. These ways include flashing LEDs (or light sources) to transmit data through to using power source analysis or noise as a transmission medium.
The Quest to Control OT Security
Once it has been accepted that the air gap as a security control is rarely valid, there is a need to aggressively deal with these connections – to either understand and bind the risks, or remove them altogether.
To achieve security control, an operational technology risk assessment is vital. Make OT security an urgent priority before your business disappears down a connection pipe you didn’t even realise was there.
Find out more about how TÜV Rheinland can help you manage your company's OT security.
For more information, speak with our experts: