In our increasingly connected world, when it comes to threat landscape and business risks, we face unprecedented challenges. In the next three years, IoT devices are expected to grow to 30 billion. According to the Boston Consulting Group, banks face 200 regulatory changes daily, as penalties for cyber threats rise to $345 billion. The average business enterprise uses 1,427 cloud services, 76 file sharing cloud services, and 210 collaboration cloud services, according to SkyHigh Magazine. A recent Hacker’s Playbook Findings Report reveals that malware attacks successfully penetrate enterprise security more than 60% of the time.
With constant security threats looming, enterprises must find a way to identify and address the risks. But how can this be done successfully when the IT landscape is continuously evolving?
Businesses Must Drive Risk Transformation
New Security analytics can support inherent risk probability analysis with the likes of Big Data, Machine Learning, Artificial Intelligence and Behavioral Analytics. Enterprises will need to start evaluating operational risk, cyber risk, and compliance risks collectively and continuously at the enterprise level, in line with Gartner’s newly defined “Integrated Risk Management” capabilities.
This presents a need to quantitatively measure current and future risks and the effects of various risk treatment approaches, including prioritisation and funding. At TUV Rheinland, here are some of the most common answers we’ve had to our questions regarding security and risk management.
How Are Decisions on Security Investments Currently Made?
- Control Assessment Gap: Picking a framework of controls and seeing if there is a gap anywhere in the organisation, and marking it red/yellow/green.
- Audit punishment alone: While audits have an excellent sense of control measures, they are not as tied in to the daily world of threat events, making them inadequate to determine effectiveness and applicability across the enterprise.
- SES (someone else’s strategy): Earlier in their career, security leaders will naturally seek advice from mentors – while helpful, it may not align with key controls for the unique sets of strategic objectives of the firm.
How Do You Select Your Key Controls and Evaluate Effectiveness?
- What are key controls?: Frequently, key controls are associated with Sarbanes Oxley or other perspectives on risk vs the advanced persistent nature of threats to your assets.
- We have meetings once a quarter: Quarterly meetings to discuss key controls are a good practice, but what decision framework is used to offer up information to aid in the decision process?
- Effectiveness is an audit call: But scope for the control is important to determine where effectiveness should be measured, a role for the risk function.
Is There a Preferred Management Framework?
Many experts in our industry agree that these are the preferred risk management frameworks:
- NIST Cybersecurity Framework
- COBITS by ISACA
- The Impact Probability Quadrant (see below)
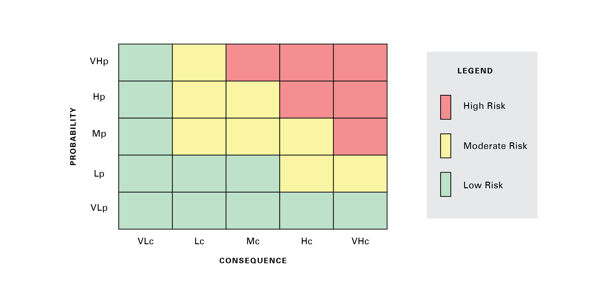
It’s important to set the stage for cyber risk prioritisation and quantification by first knowing what your potential loss scenarios are, given your business objectives and digital strategies. With a properly established and maintained risk register, you can identify cyber key controls based on real-life threat events. You can then refocus allocation of precious resources towards corporate objectives by protecting critical assets and actively monitoring residual risks.
This approach is true risk management, as opposed to reacting to gaps in a control assessment and requiring new skills and energy. For true risk management, regulatory frameworks, control framework conformance, and internal control questionnaires need to be optimised.
FAIR: A Better Way to Assess Risk
Factor Analysis of Information Risk (FAIR) is a proven methodology that speaks the language of the business and helps you prioritize what is most important in risk management. This methodology operates as both platform and open source and can operate in the “absence of data.”
The principle concepts of FAIR analysis are as follows:
- Precision versus accuracy
- Possibility versus probability
- Subjectivity versus objectivity
The FAIR methodology applies to all sectors and organisations of all sizes regardless of budget and regulatory landscape. It focuses on the organisation’s threat profile as it pertains to corporate objectives and critical assets.
For more information on cybersecurity and risk management, contact our experts:
This article first appeared on OpenSky. Click here to read the full article.