By John Ramesh, Regional Business Stream Manager (APAC IMEA), Digital Transformation & Cybersecurity, TÜV Rheinland

Achieving faster time to market, greater economies of scale and improved customer experience are only a few of the reasons organizations or industries are undergoing a digital transformation. To assure confidence, we need to improve security and speed to market, while automated testing and proactive application security provide a shift-left approach to save production cost and avoid breaches.
Market dynamics:
According to a recent market research report, the security testing market was valued at USD 3.52 billion in 2018 and is expected to register a CAGR of 27.2% during the forecast period of 2019 - 2024. The organizations are rapidly growing due to the adoption of cutting-edge solutions to enhance productivity. In order to coordinate cross-business processes and facilitate the customers in the best possible way, the organizations are deploying third-party applications wherever necessary. These third-party applications may be prone to cyber-attacks due to the variations in the security policies of different organizations. Factors such as a rise in malware and phishing threats, and growth in adoption of IoT and BYOD trend among organizations, are driving the cybersecurity industry.
Importance of Cybersecurity testing:
Cybersecurity has always been a challenge over the years and it is not going to be different in the coming years as well. The threat of frauds outsmarting enterprises’ defence mechanisms to maintain their data privacy and security are expected to shoot up. The cyberspace is now dominating our globalized economy, IoT can be a deciding or depending factor in many instances. A lot of factors such as information wars, new vulnerabilities, Big Data security, cloud storage security, IoT, Ransomware and Block-chain security, Artificial Intelligence clearly show up why cybersecurity is really important in 2019.
Adequate measures need to be taken in order to handle these concerns. It is becoming really important to increase the number of security experts to overcome these concerns and proper quality training needs to be given to them. We are expecting more interventions from governments to provide scrutiny, attention, and care. Apart from data privacy rights or net neutrality; a complete shift of focus to internet security is important. Additional steps need to be taken in the cyber and email security which can make an impact on the overall productivity of enterprises in the long run.
Our approach:
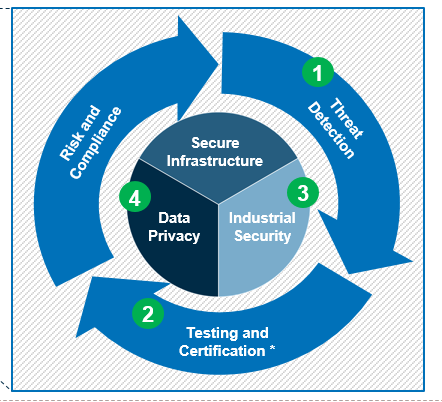
Our global, end-to-end cybersecurity services portfolio spans consulting, technology implementation, testing, managed services and certifications. Our goal is to safeguard the organizations around the world from ever-increasing cyber threats and enable safety, security, and privacy in an increasingly digital world.
TÜV Rheinland’s testing services, such as vulnerability assessments, penetration testing, and application security testing help organizations to take their security program to the next level. Our effective penetration test and IT security analysis reduce the vulnerability to potential hackers and improve the security of the network, IT systems and mobile devices. Our qualified specialists identify ways to permanently protect organizations from network attacks. With stable network security, we can ensure that our customers’ data are confidential and protected.
Network and Infrastructure:
We help organizations to design and implement a secure network with the power to face today’s cyber threats. Our services include assessments, Information Rights Management, Managed Log Collection, and Managed Threat Detection and Response services.
At the core of digital enterprise lie potential security gaps among people and technology that adversaries can exploit. To close the gaps, we need to run multiple internal and external types of tests, including penetration tests, vulnerability assessments, and social engineering. Automation alone isn’t the fix. We need the human touch of engineers and analysts who have been in the trenches and understand adversarial patterns.
Application Testing:
As web, mobile, and cloud applications proliferate, testing takes on added significance. Across all industries and environments, complete lifecycle testing solutions for development, modernization, and maintenance are essential to ensure software integrity and security. For different platforms, we need a flexible testing framework. TÜV Rheinland helps to pinpoint the exact weaknesses in the IT infrastructure to prevent these attacks. Our experts take a close look at the applications and come up with a cohesive plan to make them as secure as possible.
IoT/Embedded System Testing:
Intelligent networks between physical devices and the internet offer endless possibilities but come with many risks. Given the security intricacies that the Internet of Things (IoT) and embedded devices present, testing the hardware alone isn’t enough. The entire physical and digital ecosystem needs to be examined during the testing process. IoT/Embedded Systems Testing requires a holistic approach, which includes the testing of operational technology (OT) components. TÜV Rheinland is here to help you assess, secure and certify your IoT products and services.
Adversarial Simulation:
Along with prevention and detection, organizations should look at building response capabilities. Having the right balance among protection, detection, monitoring, and response is critical.
In contrast to traditional penetration testing and red team methodology, adversarial simulation combines multiple testing methodologies which include social engineering practices as a concentrated offensive attack. An adversarial simulation is a collaborative approach, often executed by purple teams (red and blue teams combined), to gain a comprehensive understanding of the organization’s operational effectiveness.
Our Experience:
We have a large global network of experts with extensive knowledge of testing technical guidelines, processes, network architectures, and industry-specific protocols. We have deployed our experience of penetration testing and IT security analysis successfully in a variety of industries, from small companies to major enterprises. We also have the specialist knowledge for SAP environments, mainframes, and production and process control technology.
Conclusion:
The cyber attackers are targeting vulnerable applications and harming the valuable assets of organizations. We have seen significant growth in the adoption of security testing solutions to detect and mitigate security vulnerabilities. The organizations should look forward to deploying security testing solutions to align strategic business activities to minimize the damage of IT resources which will provide the major opportunity for market growth.